Ransomware 101: What Every SMB Owner Must Know
Imagine a typical morning at your small business: you’re ready to start the day, check emails, and serve customers. Suddenly, you can’t access your files, and a message demands payment in exchange for a decryption key. This scenario is not just a plot from a cyber-thriller; it’s the harsh reality of ransomware, a type of malware that has increasingly targeted small and medium-sized businesses (SMBs). Ransomware attacks can cripple operations, leading to significant financial losses and damage to your business’s reputation.
Table of Contents
The Evolution of Ransomware Attacks
In the early 2010s, a notable shift occurred with the emergence of ransomware like CryptoLocker. These new strains of ransomware employed advanced encryption algorithms to lock access to the victim’s files and demanded a ransom, typically in cryptocurrency, for the decryption key. This marked a transition from mere inconvenience to serious cyber threats, as victims risked losing valuable or sensitive data permanently. The success of CryptoLocker and its variants inspired a wave of similar ransomware attacks, each more sophisticated than the last. This era saw the rise of ransomware as a service (RaaS), where malware creators lease out ransomware to other criminals, further proliferating the threat.
The financial impact of ransomware has grown exponentially. According to a report by Cybersecurity Ventures, ransomware damages, which include downtime, lost productivity, and the cost of the ransoms themselves, are projected to cost a staggering $265 Billion by 2031. This astronomical figure highlights the lucrative nature of these attacks for cybercriminals and underscores the critical need for robust cybersecurity measures. Small and medium-sized businesses (SMBs) are particularly vulnerable, often lacking the resources for comprehensive cyber defense strategies. This vulnerability has made them prime targets for ransomware attackers. The evolution of ransomware signifies not just a technological advancement in malware but also a shift in the cyber threat landscape. Businesses, regardless of size, must now consider ransomware a top security priority, investing in both preventive measures and recovery plans to mitigate the potentially devastating consequences of an attack.
How Ransomware Works?
1. Infiltration
The initial breach is often the result of seemingly innocuous activities:
- Phishing Emails: These are cleverly disguised as legitimate communications, enticing unsuspecting employees to click on malicious links or download infected attachments.
- Exploit Kits: These are automated tools that probe for vulnerabilities in software and systems. Once a weakness is detected, the exploit kit delivers the ransomware payload.
- Remote Desktop Protocol (RDP) Vulnerabilities: RDP, a popular remote access tool, can be a gateway for attackers if not properly secured. Cybercriminals exploit weak or stolen RDP credentials to gain unauthorized access.
2. Establishment
Upon successful entry, the ransomware quietly embeds itself in the system. During this phase, it may:
- Lay Dormant: Some sophisticated ransomware can remain undetected, waiting for the optimal time to activate.
- Spread Laterally: The malware often seeks to maximize damage by spreading to connected systems and networks.
3. Encryption
This is the hallmark of ransomware. The malware:
- Targets Specific File Types: Documents, databases, and other critical files are encrypted, rendering them inaccessible.
- Uses Strong Encryption Algorithms: Modern ransomware employs complex encryption methods, making it nearly impossible to decrypt files without the unique key held by the attacker.
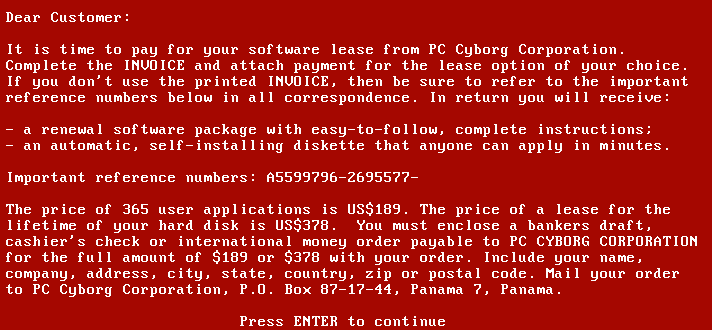
4. Ransom Demand
Once the data is encrypted, the ransomware reveals its presence:
- Ransom Note: Victims are presented with a message explaining that their data has been encrypted and demanding a ransom, typically in cryptocurrency, for the decryption key.
- Payment Instructions: The note often includes detailed instructions on how to pay the ransom, sometimes with a deadline and threats of data deletion or exposure.
5. Communication with Attackers
Some ransomware variants establish a communication channel:
- Payment Negotiation: Attackers may provide an email address or anonymous messaging system to negotiate payment.
- Decryption Key Delivery: If the ransom is paid, the attackers may provide a decryption key to unlock the files, though this is not guaranteed.
Why SMBs are Targeted by Ransomware?
Small and medium-sized businesses (SMBs) have become prime targets for ransomware attacks, and understanding why requires a look into the unique vulnerabilities they often possess. Unlike larger corporations, SMBs typically operate with more limited resources, particularly in their IT departments. This constraint leads to a situation where cybersecurity measures might not be as robust or up-to-date as they should be. Many SMBs lack dedicated cybersecurity staff, and the responsibility for managing IT security often falls on employees who may not have specialized training in this area.
Another factor contributing to the vulnerability of SMBs is the misconception that they are too small to be noticed by cybercriminals. This false sense of security can lead to complacency in implementing stringent security protocols. However, the reality is quite the opposite. Cybercriminals are aware that SMBs are less likely to have sophisticated defense mechanisms, making them easier targets compared to larger organizations with more fortified security infrastructures.
Furthermore, SMBs are often part of larger supply chains and may have access to the networks of bigger companies. Attackers exploit SMBs as entry points to infiltrate these larger networks, where they can potentially cause more significant damage and extract larger ransoms. This interconnectedness increases the attractiveness of SMBs to cybercriminals.
Impact of Ransomware on Small and Medium Businesses
The impact of ransomware on small and medium-sized businesses (SMBs) extends far beyond the immediate disruption and potential financial loss due to the ransom itself. When an SMB falls victim to a ransomware attack, the consequences can ripple through every aspect of its operations, often with long-term effects.
Financially, the burden of a ransomware attack is multifaceted. The most obvious is the ransom demand, which can range from a few thousand to hundreds of thousands of dollars, a significant amount for any SMB. However, even if the ransom is paid, there’s no guarantee that the data will be fully recovered or that the attackers won’t leave behind hidden malware. Beyond the ransom, SMBs face the cost of downtime. During an attack, critical systems and data become inaccessible, halting operations. For businesses that rely heavily on daily transactions, such as retail or services, this downtime can lead to substantial revenue loss. Additionally, the cost of professional services for incident response, forensic investigation, and system restoration adds to the financial strain.
The operational impact is equally devastating. A ransomware attack can paralyze an SMB’s operations, affecting every facet from customer service to supply chain management. The time and resources required to address the attack often mean that normal business activities are pushed to the sidelines, leading to lost opportunities and strained business relationships. For businesses that handle time-sensitive data or transactions, the delay caused by ransomware can have cascading effects, disrupting schedules and commitments.
Legal and reputational consequences are also significant considerations. Depending on the nature of the data compromised, SMBs may face legal penalties for breaches of customer or employee data privacy. Compliance with various data protection regulations, such as GDPR in Europe or HIPAA in the United States, becomes a complex issue post-attack. The reputational damage can be even more harmful in the long run. Customers and partners may lose trust in an SMB that has fallen victim to a ransomware attack, especially if it leads to the compromise of sensitive data. Rebuilding this trust can take years and requires substantial investment in both security infrastructure and public relations efforts.